Data Security Assessment: Strengthening Your Cyber Defense
Data Security Assessment: Strengthening Your Cyber Defense
Blog Article
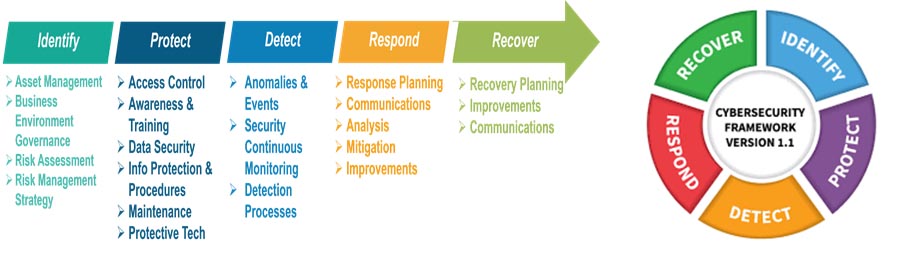
A Data Security Assessment (DSA) is a systematic evaluation of an organization's data security measures to identify vulnerabilities, assess risks, and ensure compliance with industry standards. With cyber threats evolving rapidly, businesses must proactively assess their security posture to protect sensitive information from breaches, unauthorized access, and data loss.
Why is Data Security Assessment Important?
1. Identifying Security Gaps
- Detects weaknesses in security controls, access management, and network protection.
- Helps prevent cyber threats such as malware, ransomware, and phishing attacks.
2. Compliance and Regulatory Adherence
- Ensures alignment with data security regulations such as GDPR, CCPA, HIPAA, PCI DSS, and ISO 27001.
- Avoids potential fines, legal issues, and reputational damage.
3. Enhancing Incident Response Preparedness
- Improves the organization’s ability to detect, respond to, and recover from security incidents.
- Strengthens disaster recovery and business continuity plans.
Key Components of a Data Security Assessment
1. Data Classification and Inventory
- Identifying and categorizing sensitive data, including personal, financial, and intellectual property.
- Mapping data flow across on-premises, cloud, and third-party environments.
2. Threat and Risk Analysis
- Assessing potential cyber threats, including external attacks and insider threats.
- Evaluating the impact and likelihood of data breaches.
3. Security Controls Evaluation
- Reviewing encryption standards, access controls, and authentication mechanisms.
- Assessing the effectiveness of firewalls, endpoint protection, and intrusion detection systems (IDS).
4. Vulnerability Assessment and Penetration Testing (VAPT)
- Identifying security vulnerabilities through automated scanning and manual testing.
- Simulating cyberattacks to evaluate the organization’s defense mechanisms.
5. Compliance and Policy Review
- Auditing data security policies, incident response plans, and governance frameworks.
- Ensuring employees follow security best practices and regulatory requirements.
6. Employee Awareness and Training
- Conducting security awareness programs to mitigate human errors and social engineering risks.
- Implementing phishing simulations and cybersecurity training sessions.
Steps to Conduct a Data Security Assessment
1. Define the Assessment Scope
- Determine which systems, applications, and data assets will be assessed.
2. Perform Data Discovery
- Identify where critical data is stored and who has access to it.
3. Conduct Risk Analysis
- Evaluate the likelihood and impact of security threats.
4. Test and Analyze Security Controls
- Use vulnerability scanning and penetration testing to assess weaknesses.
5. Implement Security Enhancements
- Strengthen encryption, update access controls, and remediate vulnerabilities.
6. Document Findings and Develop an Action Plan
- Generate a report with recommendations for improving security.
7. Monitor and Continuously Improve
- Regularly update security policies and conduct periodic assessments.
Best Practices for Effective Data Security
- Adopt a Zero-Trust Security Model: Require continuous verification for users and devices.
- Use Multi-Factor Authentication (MFA): Strengthen user authentication measures.
- Encrypt Data at Rest and in Transit: Protect sensitive information from unauthorized access.
- Regularly Patch and Update Systems: Mitigate vulnerabilities by keeping software up to date.
- Backup Data Frequently: Ensure resilience against ransomware and accidental data loss.
Conclusion
A Data Security Assessment is essential for safeguarding sensitive information and maintaining regulatory compliance. By proactively identifying risks, strengthening security controls, and fostering a security-conscious culture, organizations can reduce cyber threats, enhance resilience, and protect their digital assets. Regular assessments ensure continuous improvement, helping businesses stay ahead of emerging security challenges. Report this page